Wi-Fi security recently took on the ultimate challenge at the infamous Black Hat USA 2015 security conference held this year at Mandalay Bay in Las Vegas.
One of the world’s premiere hacking events, Black Hat attracts some 10,000 security super geeks who like to break stuff.
Wi-Fi has always been a prime security target for Black Hat, who describes the network “the most hostile Wi-Fi network in the world.” And this year was no different. So Black Hat wanted to do something unique, something better.
Wi-Fi security recently took on the ultimate challenge at the infamous Black Hat USA 2015 security conference held this year at Mandalay Bay in Las Vegas.
One of the world’s premiere hacking events, Black Hat attracts some 10,000 security super geeks who like to break stuff.
Wi-Fi has always been a prime security target for Black Hat, who describes the network “the most hostile Wi-Fi network in the world.” And this year was no different. So Black Hat wanted to do something unique, something better.
 So we took the challenge, teaming with RG Nets, a little known but super sophisticated Wi-Fi application gateway innovator, to create a virtually unhackable network.
So we took the challenge, teaming with RG Nets, a little known but super sophisticated Wi-Fi application gateway innovator, to create a virtually unhackable network.
 The Black Hat Wi-Fi network is infamous as a playground for attendees to try out the latest hacking tools against not only the greater Internet, but each other. Black Hat faced two fundamental challenges:
The Black Hat Wi-Fi network is infamous as a playground for attendees to try out the latest hacking tools against not only the greater Internet, but each other. Black Hat faced two fundamental challenges:
- providing high-speed, high density Wi-Fi connectivity to delegates while
- ensuring bullet-proof Wi-Fi security that could prevent attendees from using the Wi-Fi to compromise the entire network and each other.
 Wireless client isolation somewhat mitigates this problem, but only within a single access point. Traditional network segmentation techniques such as implementing a handful of VLANs fail to create enough isolation between clients. Even "modern" VLAN pooling systems often fail to sufficiently minimize the number of devices that can talk to each other in high density environments, due to lazy assignment algorithms and a limited number of supported VLANs. The ideal solution for maximum security between users is to tag each device's traffic with its own unique VLAN ID, which effectively places each user in his or her own "sandbox" network. This per-device VLAN strategy prevents a would-be attacker from harming the network infrastructure and other users by making ARP spoofing, IP address conflicts, rogue DHCP servers, network scans, and other attacks and exploits irrelevant against anyone but themselves.
So Ruckus teamed up with RG Nets to create a safer and more reliable high-density Wi-Fi network by utilizing a fancy dynamic VLAN assignment and routing engine to provide thousands of isolated networks for Black Hat attendees.
The real goal was not only to try and provide secure, high-speed Wi-Fi, but also find a way to automate an 802.1X framework that provides AES-level encryption and authentication while dynamically assigning each device or a group of devices to a discrete VLAN.
Wireless client isolation somewhat mitigates this problem, but only within a single access point. Traditional network segmentation techniques such as implementing a handful of VLANs fail to create enough isolation between clients. Even "modern" VLAN pooling systems often fail to sufficiently minimize the number of devices that can talk to each other in high density environments, due to lazy assignment algorithms and a limited number of supported VLANs. The ideal solution for maximum security between users is to tag each device's traffic with its own unique VLAN ID, which effectively places each user in his or her own "sandbox" network. This per-device VLAN strategy prevents a would-be attacker from harming the network infrastructure and other users by making ARP spoofing, IP address conflicts, rogue DHCP servers, network scans, and other attacks and exploits irrelevant against anyone but themselves.
So Ruckus teamed up with RG Nets to create a safer and more reliable high-density Wi-Fi network by utilizing a fancy dynamic VLAN assignment and routing engine to provide thousands of isolated networks for Black Hat attendees.
The real goal was not only to try and provide secure, high-speed Wi-Fi, but also find a way to automate an 802.1X framework that provides AES-level encryption and authentication while dynamically assigning each device or a group of devices to a discrete VLAN.
 This would require a close interworking between a cluster of Ruckus WLAN controllers, Ruckus SCGs in this case, and the RG Nets rXg Wireless Application Gateway system.
RG Nets configured its system to act as a firewall in between the Ruckus SCG and rXg clusters. The wired network to which the Ruckus APs were connected was completely locked down. The MAC address OUIs of the Ruckus APs were programmed into the rXg system.
This ensured that only the Ruckus APs authorized could utilize the wired network and communicate with the rXg's RADIUS server. Routing out the Internet was completely disabled on the wired network. This was particularly important for Black Hat because it was very easy to sit on the floor in the Mandalay Bay conference area, unplug an AP, and instead connect a laptop via Ethernet to the same wired fabric. Disconnected APs were actively monitored throughout the event. Any "missing" AP MAC addresses were blacklisted to prevent someone from spoofing the MAC address of an AP and gaining access to the management network.
HOW IT ALL WORKED
When any Black Hat user associated with the Ruckus Wi-Fi network, a RADIUS 802.1X request would be sent from the Ruckus controller to the in-line rXg system that would then dynamically assign each user, or a small group of users, to a unique VLAN that would follow them wherever they roamed.
The rXg is able, among a myriad of sophisticated packet processing chores, to support thousands of dynamic VLAN assignments, allowing each user, if needed, to have their own logical network, while keeping track of each user and their VLAN assignment.
With 802.1X MAC authentication configured on the Ruckus WLAN controllers, when a client tried to access the Wi-Fi network using a pre-shared key, the rXg system would receive a RADIUS access request from the WLAN cluster.
That access request contains the client’s MAC address and some other information used by the rXg to assign a VLAN tag. The rXg then responded to the Ruckus controllers with a RADIUS Access-Accept response that contains the VLAN ID for each client or group of clients.
Using this information from the rXg, the Ruckus WLAN controllers accepted the connection from the client and each AP would then tag client traffic with the assigned VLAN ID.
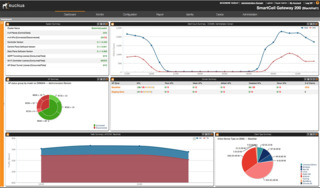
With all the traffic trunked to the Ruckus WLAN cluster and rXg system, the architecture proved to be extremely secure and successful, drastically reducing the attack “surface area” at Black Hat.
If compromised, a hacker would be able to “see” users and services only within a particular VLAN and not the entire network. So each user or user group effectively had their own virtual network that could follow them around coupled with AES encryption on the airlink. Wow.
And to ensure consistent, high-speed connectivity and fair use of the available wired and wireless bandwidth available, the rXg was also configured to provide per-device bandwidth queuing of 20Mbps down and 10Mbps up.
What’s more, the rXg cluster was also used to provide DHCP to Black Hats from a pool of public IPs, while controlling the routing of traffic to the Internet and preventing delegates from attacking the Ruckus controllers or APs.
A double SSH tunnel (VPN) through the rXg cluster was utilized to securely gain access to the RG Nets and Ruckus management consoles over the Wi-Fi network. SSH was blocked on the network as well other than from specific laptops. And SSH and HTTPS anomaly detection was enabled on the rXg just to be safe.
BLOCKING THE BAD BOYS
Ultimately, hundreds of malicious network scans and malware proliferation attempts were detected by the rXg and a variety of malicious events that would have turned into greater problems for network stability, were blocked. These events usually entail wide use of many types of attacks, particularly DoS, ARP spoofing, traffic storms, etc.
Behavioral connection IPS, using fancy heuristics, was used to block all sorts of malicious activity. rXg's DPI engine was configured with emerging threat signatures to detect intrusion attempts, malware, etc. Before the event was over nearly 1000 instances of threat signatures occurred on the network, which is far more than other conference environments.
SECURE HIGH DENSITY WI-FI DELIVERED
The AP network, consisting of some 80 Ruckus 802.11ac Smart Wi-Fi access points managed by a cluster of Ruckus SCG controllers, was never compromised, and no notable attacks or exploits were reported between Wi-Fi end-users due to the implementation of VLAN client isolation.
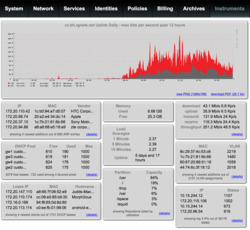
Data use at Black Hat was higher than average for a typical conference. Over 3 terabytes of traffic was routed over the Ruckus Wi-Fi network during the event. SSL traffic made up over half of all data usage, as many of the delegates who were brave enough to connect to the Wi-Fi encrypted their connections through an external VPN.
During the conference, the network operations team saw concurrent Wi-Fi client connections peak to over 2300 with some APs able to take on 300 simultaneous users with no performance compromises.
So yes, we’ve been asked back next year.
This would require a close interworking between a cluster of Ruckus WLAN controllers, Ruckus SCGs in this case, and the RG Nets rXg Wireless Application Gateway system.
RG Nets configured its system to act as a firewall in between the Ruckus SCG and rXg clusters. The wired network to which the Ruckus APs were connected was completely locked down. The MAC address OUIs of the Ruckus APs were programmed into the rXg system.
This ensured that only the Ruckus APs authorized could utilize the wired network and communicate with the rXg's RADIUS server. Routing out the Internet was completely disabled on the wired network. This was particularly important for Black Hat because it was very easy to sit on the floor in the Mandalay Bay conference area, unplug an AP, and instead connect a laptop via Ethernet to the same wired fabric. Disconnected APs were actively monitored throughout the event. Any "missing" AP MAC addresses were blacklisted to prevent someone from spoofing the MAC address of an AP and gaining access to the management network.
HOW IT ALL WORKED
When any Black Hat user associated with the Ruckus Wi-Fi network, a RADIUS 802.1X request would be sent from the Ruckus controller to the in-line rXg system that would then dynamically assign each user, or a small group of users, to a unique VLAN that would follow them wherever they roamed.
The rXg is able, among a myriad of sophisticated packet processing chores, to support thousands of dynamic VLAN assignments, allowing each user, if needed, to have their own logical network, while keeping track of each user and their VLAN assignment.
With 802.1X MAC authentication configured on the Ruckus WLAN controllers, when a client tried to access the Wi-Fi network using a pre-shared key, the rXg system would receive a RADIUS access request from the WLAN cluster.
That access request contains the client’s MAC address and some other information used by the rXg to assign a VLAN tag. The rXg then responded to the Ruckus controllers with a RADIUS Access-Accept response that contains the VLAN ID for each client or group of clients.
Using this information from the rXg, the Ruckus WLAN controllers accepted the connection from the client and each AP would then tag client traffic with the assigned VLAN ID.
With all the traffic trunked to the Ruckus WLAN cluster and rXg system, the architecture proved to be extremely secure and successful, drastically reducing the attack “surface area” at Black Hat.
If compromised, a hacker would be able to “see” users and services only within a particular VLAN and not the entire network. So each user or user group effectively had their own virtual network that could follow them around coupled with AES encryption on the airlink. Wow.
And to ensure consistent, high-speed connectivity and fair use of the available wired and wireless bandwidth available, the rXg was also configured to provide per-device bandwidth queuing of 20Mbps down and 10Mbps up.
What’s more, the rXg cluster was also used to provide DHCP to Black Hats from a pool of public IPs, while controlling the routing of traffic to the Internet and preventing delegates from attacking the Ruckus controllers or APs.
A double SSH tunnel (VPN) through the rXg cluster was utilized to securely gain access to the RG Nets and Ruckus management consoles over the Wi-Fi network. SSH was blocked on the network as well other than from specific laptops. And SSH and HTTPS anomaly detection was enabled on the rXg just to be safe.
BLOCKING THE BAD BOYS
Ultimately, hundreds of malicious network scans and malware proliferation attempts were detected by the rXg and a variety of malicious events that would have turned into greater problems for network stability, were blocked. These events usually entail wide use of many types of attacks, particularly DoS, ARP spoofing, traffic storms, etc.
Behavioral connection IPS, using fancy heuristics, was used to block all sorts of malicious activity. rXg's DPI engine was configured with emerging threat signatures to detect intrusion attempts, malware, etc. Before the event was over nearly 1000 instances of threat signatures occurred on the network, which is far more than other conference environments.
SECURE HIGH DENSITY WI-FI DELIVERED
The AP network, consisting of some 80 Ruckus 802.11ac Smart Wi-Fi access points managed by a cluster of Ruckus SCG controllers, was never compromised, and no notable attacks or exploits were reported between Wi-Fi end-users due to the implementation of VLAN client isolation.
Data use at Black Hat was higher than average for a typical conference. Over 3 terabytes of traffic was routed over the Ruckus Wi-Fi network during the event. SSL traffic made up over half of all data usage, as many of the delegates who were brave enough to connect to the Wi-Fi encrypted their connections through an external VPN.
During the conference, the network operations team saw concurrent Wi-Fi client connections peak to over 2300 with some APs able to take on 300 simultaneous users with no performance compromises.
So yes, we’ve been asked back next year.